It’s the year 2020. A new decade is upon us, and the time for progress is now. Commercial spaceflight is becoming a reality, consumers are buying electric cars, cell phones with more RAM than desktop PCs will soon be released, but some things never change either…
What never changes? Our reliance on internet connected devices, and ultimately the possibility for security risks and vulnerabilities in those devices, that allow for malicious exploits to be run against a network.
What is it?
The latest critical vulnerability has been named Cable Haunt, specifically because it affects cable modems and modem/router combos from a number of manufacturers throughout the world. The word haunt is used because the exploit has existed within these devices, silently, for many years now, and has only recently been discovered. This could impact around 200 million cable modem users.

Discovered by Lyrebirds, a cyber security company in Denmark, they have created a website to address and discuss the vulnerability and have included a deep dive technical report (available here) as well as a proof of concept and test script you can run against your own network to see if your modem is vulnerable.
What could it do?
Cable Haunt is exploited by first gaining access to a local network device like a computer, though it could be any device on the LAN. This can be via a number of methods and is outside the scope of this document for now. Once the local device is compromised, a buffer overflow attack is initiated against the modem, ultimately giving the attacker control of the cable modem.
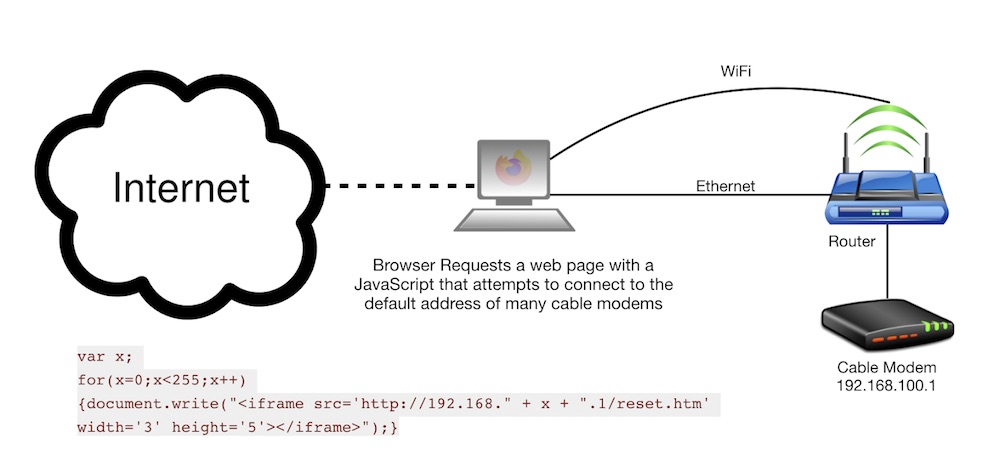
CableHaunt specifically attacks a tool built into modems called Spectrum Analyzer. A flaw in Spectrum Analyzer allows an attacker to send HTTP requests to the modem, regardless of the local device they’ve attacked first. Once the buffer overflow is in place the modem is under the attackers control, and they could perform a number of malicious changes including; updating DNS servers to point end users to malicious versions of legitimate web sites, man in the middle attacks, changing firmware, and more
How to protect against it?
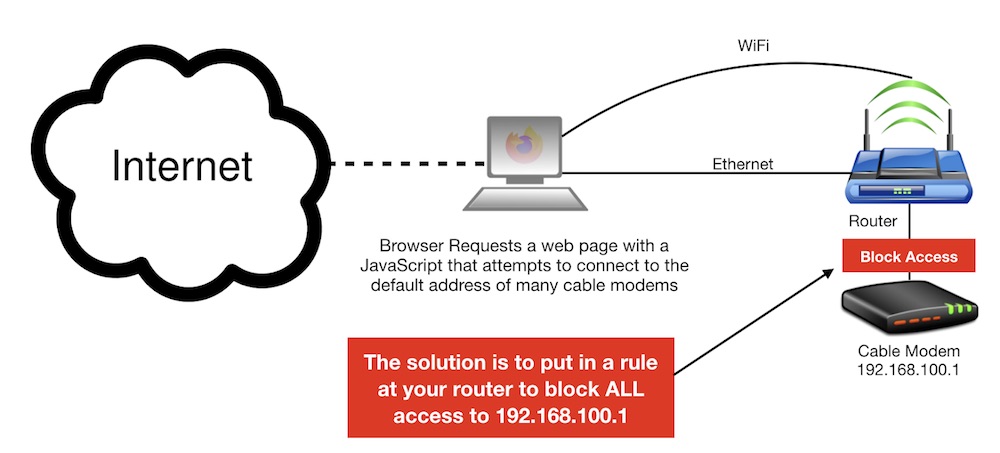
Since Cable Haunt is dependent on first taking control of a local device, it is possible to configure many routers to block local access to the vulnerable modem. If access to the cable modem is prevented, there isn’t a way to actively exploit Cable Haunt. We’ll cover a few different router manufacturers here with screenshots on how to make these changes. TIP: A downside to this firewall rule is you won’t be able to access your modem either. You could modify these rules to block only the port that the Spectrum Analyzer runs on, but if you replace your modem and a different port is used, you’ll no longer be protected without first updating created rules.

First, it is important to determine IF your device is vulnerable. Currently, only devices running Broadcom equipment are affected. If your device is NOT manufactured with Broadcom components, you are safe! You can visit Approved Modems for a list of manufacturers and devices to determine if you are affected.

Peplink/Pepwave
- Log into the web administration interface at 192.168.1.1 (Pepwave) or 192.168.50.1 (Peplink). If you have changed your LAN IP, please use the new address.
- Log in, and visit the Advanced (Pepwave) or Network (Peplink) tab, and select Firewall: Access Rules, from the left menu.
- On the right of the screen, you’ll see sections for Outbound Firewall Rules, Inbound Firewall Rules, and Internal Network Firewall rules, along with any existing rules that are in place.
- Click Add Rule under Outbound Firewall Rules
- Create a rule named Cable Modem Block and follow the screenshot below. Important here is setting the Action to Deny, and enabling Event Logging for later review. Click Save.
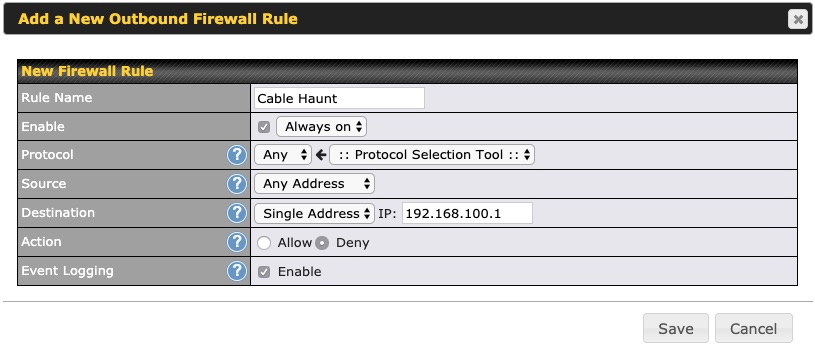
- The firewall rules are set up with the highest priority rules listed first, so click and drag the newly created Cable Haunt rule to the top of the list. Be sure to click Apply Changes in the top right corner of the web administration interface.
- Special note – If your cable modem uses a different default address other than 192.168.100.1, be sure to modify this rule to the appropriate IP address.
How do I log into my Peplink/Pepwave if I disable local access?
InControl is Peplinks cloud management platform which provides monitoring, configuration, and remote access, to all of your Peplink/Pepwave hardware from a single sign on. If you are a business and are deploying Pep equipment across multiple sites, InControl can manage them all. You’ll have real time views into network performance, internet connection status, client lists, data usage, and more. You can remotely configure and push configurations such as WiFi updates, firewall settings, and firmware updates.
When it comes to Cable Haunt, InControl gives you a simple means of remotely accessing your local router interface with their Remote Management feature. A simple firewall rule, as described above, blocks local devices from executing Cable Haunt vulnerabilities. With InControl, you can still log into the router, manage and make changes, all securely. You can follow this link for the InControl 2 user manual.
Learn more about Peplink/Pepwave products and services at 5Gstore

Cradlepoint
- Log into the web administration interface at 192.168.0.1. If you have changed the default address, please use the new address.
- Log in, and visit the Security tab on the left side of the page, and click Filter Policies.
- You’ll see a few basic Filter Policies in place depending on your configuration. Click Add.
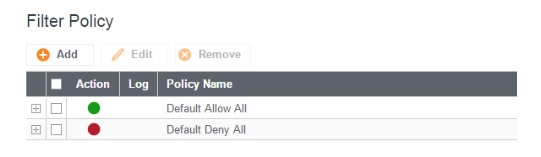
- Name your filter Cable Modem Block, set the default action to Deny, and select Log to enable logging to the router for later review.
- Enter a source address of 0.0.0.0 for all LAN clients. Destination is the IP address of your cable modem, typically 192.168.100.1, but be sure to modify if you’ve changed this.
- Click save, and then Apply Changes.
- For a full breakdown of the Cradlepoint Firewall, visit Cradlepoint Connect.
How do I log into my Cradlepoint if I disable local access?
NetCloud Manager is the Cradlepoint cloud management platform. NetCloud performs the functions you would expect from the cloud; firmware management, device configuration, status, alerts, and more.
Cradlepoint no longer sells hardware on its own, and instead offers solutions packages that include technical support, warranty, and access to NetCloud. You can follow this link for a guide on using NetCloud, including local administration and cloud management.
Learn more about Cradlepoint and NetCloud services at 5Gstore
Sierra Wireless
Sierra wireless doesn’t have a typical stateful firewall built into its web administration interface. You can not explicitly tell the router ‘block outbound traffic to 192.168.100.1.’ Instead, you can block ALL outbound traffic, and create a list of Trusted IPs that can be accessed by local devices. This means making a rule for ALL IPs you wish to visit, which can be cumbersome. This is not a problem though, as typically you are NOT using a cable modem along with the Sierra product line. Cellular is the typical primary connection and is not affected.
If you do have a Sierra with a connected cable modem, you’ll need to add a firewall appliance like a Sonicwall or similar, in order to block access to the modem from the local network.
Other Manufacturers
Michael Horowitz of RouterSecurity.org has an excellent in-depth article on blocking cable modems from various manufacturers such as TP Link and Asus. If your specific model isn’t listed, it doesn’t mean the same general rules won’t apply.
Additional Considerations
Q: What if I have a cable modem/router combo provided by my ISP, and it is in Bridge or IP Passthrough mode, am I affected?
A: Putting a modem/router combo in Bridge mode won’t necessarily prevent you from a Cable Haunt attack. Some devices still run their web servers while in passthrough, which leaves an open means of attack. Don’t assume everything is okay, test!
Basic Testing
While not perfect, a quick test in a web browser can help determine if a network is potentially vulnerable to Cable Haunt. This can be done on a desktop PC, laptop, or phone, that is wired or connected via WiFi to the network you wish to test.
- Open up a web browser of your choice (Chrome, Firefox, Safari, etc)
- In the address bar, enter the corresponding default IP Address from this list
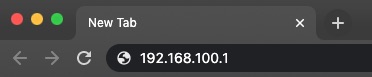
- f the page loads to a login screen, the network is potentially susceptible to Cable Haunt.
Advanced Testing – IT Professionals Only
The folks behind Lyrebirds, the organization that found this vulnerability, have developed a script to let network administrators test their modem for Cable Haunt. They’ve posted the script and Python code to their GitHub repository for download.
Fair warning, this is a ‘use at your own risk’ tool and should only be utilized on networks that you own or have explicit authority to test. Ultimately, this test will cause a vulnerable cable modem to crash and reboot if the device is found to be vulnerable. Therefore, do not perform this testing during business hours or times when internet connectivity is critical.
Lyrebirds have posted a video showing an active exploit against a Cable Haunt vulnerable modem in a test environment. In just a few minutes you can see how their GitHub testing script works, and just how quickly a knowledgeable attacker could gain access to a modem completely undetected in most cases.

